Access Control to Biometric Services such as to banking, telecommunications and health services.
CORE platform for identity validation through BIOMETRIC (finger or facial)
CORE platform for biometrics

ByCASB is a platform developed by Bytte® to authenticate the identity of clients or users, whether from the banking sector or entities providing health services, financial services, insurance, etc. In order to authorize the provision of the service and / or delivery of products to authorized beneficiaries, aimed at reduce fraud by identity theft or as support for environmental sustainability policies aimed at managing zero paper, all in Cloud architecture Computing  .
.
ByCASB allows:
- Handling of high traffic devices to capture basic information of the document carrier from 1D and 2D barcodes, with image analysis on the back of the document based on mathematical processes to detect adulterations and / or modifications in the printed information.
- User enrollment and identity authentication aimed at minimizing fraud by spoofing.
- Management of the authentication process in local conditions when problems of interconnection with the NUBE arise.
- Access to information online with the result of the authentication process for analysis and statistics.
- It allows the integration in an easy way to the client's Core systems.
ByCASB process of identity validation using fingerprint biometrics:
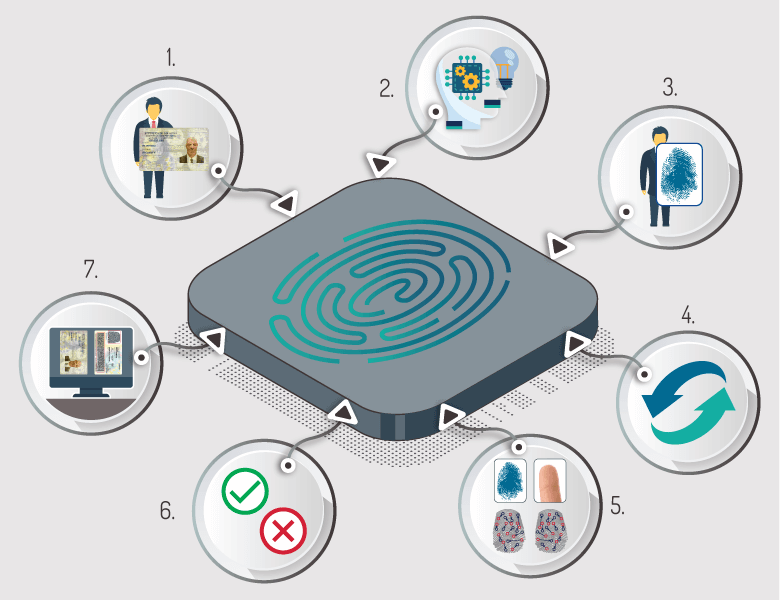
- Document Request: The beginning of the enrollment process begins with the request for the identity document of the Client or user.
- Reading of the PDF417 barcode to extract the biographical information (Names, Surnames, Document Number, Date of Birth, RH, Sex) and digitalization of the back of the identity document [1] in order to perform an image analysis process to determine the basic characteristics of the document in order to detect adulterations and / or modifications, if these validations are successful, the system proceeds to extract the minutiae from the printed image of the trace (characteristic points of the fingerprint) in order to perform the identity authentication of the document bearer.
- Customer's fingerprint request, through this step the client or user is requested to place the fingerprint in the biometric reader in order to extract the detail in real time.
- Comparison of the template (or characteristic points of the fingerprint) extracted from the image of the document versus the template of the live finger to determine the identity of the bearer of the document.
- Manual comparison of the biographical information extracted in step II of the document (Names, Surnames, Document Number, Date of Birth, RH, Sex) versus the one printed.
- Total result of the process (Successful or not successful): if the entire process is successful, the system will inform that the authentication was done in the correct way, otherwise the system will inform that the transaction is rejected.
- Storage of the transaction in the information system: Independent of the result of the process the transaction will be stored in the system.
Considerations:
The operators of the authentication tool must follow a procedure pre-established by the entity to process the cases of failed authentication in order to determine the cause or reason for the rejection since it can be given for two reasons:
- Attempt of fraud.
- False Rejection: that is to say that the user is the one who says it is but due to other factors such as mutilations, skin diseases (dermatitis), wear of fingerprints due to age, loss of fingerprints due to manipulation of corrosive materials, imprint of the card very pixilated or deteriorated etc., which generate failure in the process of identity authentication, for which second level processes should be generated (type retro questions) in order to validate the identity of the person who does not pass the process of fingerprint authentication.
